I find an “Unsettled Question of Offense vs Defense in Cyberwarfare” article quite misleading. For example it frames the problem state as this:
…there is the belief that cyber weapons are different in that they favor the offense. Cited for advancing this argument are the plethora of computer vulnerabilities, the low financial cost of hacking, and the lack of penalties for discovered attacks.
Simply turn that around and the attackers are riddled with vulnerabilities, are inexpensive to counter-attack, and penalties are minimal if discovered.
Ok, so the last point may not be true, which is why defensive teams tend to never talk about defensive measures used to counter-attack and “destroy” attackers (where disclosure can sometimes mean destruction of the defensive tactic).
More to the point, it hasn’t been proven beneficial for defensive teams to expose counter-attack methods, and that gives the impression of a debate being unsettled.
While some might say there’s a deterrence possibility for exposing defensive capabilities, a much larger issue is counter-attacks are rendered less-effective when known beforehand. Also any counter-attacks given widespread exposure, or self-defense methods if you will, can get mired in legal and regulatory channels that take a very long time to resolve.
We’ve written about strategic advantages of active defense for almost a decade on this site, so hopefully it’s not news to anyone.
Also I find the article’s cyberwar definition a bit wobbly:
Cyberwar, like its regular counterpart, requires material damage such as destroying assets, disabling weapons that rely on digital components, and disabling the critical infrastructures that power the machinery of war. It is these physical effects, and how they complement military actions, which determine whether a weapon is defensive or offensive in nature.
Physical effects don’t determine defense or offense. Cyberwar doesn’t require material damage any more than a tradewar does.
And I disagree here too:
If the offense has the advantage in penetrating systems, the defense has an offsetting advantage in understanding their own complex systems.
As I said above while the defense may have the advantage in penetrating attacker systems, an attacker also may understand defensive systems better than the defense.
I’ve seen many defensive teams mostly unaware of how their own environment works, while attackers (or auditors for that matter) spend significant time documenting things carefully to prepare their best entry point and cascading damage. Heartland is a great example of this. The exfiltration of cardholder data was masterfully baked into existing business processes and therefore undetected.
Here again, I disagree:
Not only do cyber weapons require specialized skills to deploy, but the operator must also understand the targeted analog system to achieve their desired effect.
Many weapons are commodity based now and used blindly. Metasploit brought the skill level down dramatically, for example. Load a new module to the running platform, fire and forget. Some weapons are so unskilled and untargeted they’re running all the time all over the Internet just hoping someone, like an oil platform or a factory, becomes a victim.
Finally, on this next point I agree somewhat:
…we do not know what effect cyber weapons will have on mechanical military systems, their tactical or strategic value in war, or how lasting those effects will be…
Hard to predict the future, yes. However we have a pretty good idea that any system lacking basic controls by default (e.g. authentication) will be devastated by simple attacks as well as hard to defend against (e.g. people grabbing weak templates and deploying faster than fixes or configurations can be updated).
The chance of widespread outage on weak systems makes cyberweapons of strategic value, both for attackers and defenders. Although I believe we will continue to hear a lot of news about attackers exploiting vulnerabilities, and little to nothing about defenders doing the same.
Case in point, there’s a very recent BBC story in India:
fraudsters had the tables turned on them as YouTuber Jim Browning was able to hack into the call centre and access recordings of scam phone calls and even watch live CCTV footage exposing the criminals at work… Indian police raided the premises of Faremart Travel Private Limited in Gurugram, within hours of the videos being released.
Further back in 2013, there’s a story that nobody reported about the giant PR campaign “skyjack” being vulnerable on launch. Skyjack very proudly accumulated press names like a tin-pot dictator in a polyester suit covered with shiny badges:
Press: Ars Technica TechCrunch BBC NBC Huffington Post VICE Mashable Gizmodo Engadget Gizmag NewScientist The Escapist Tom’s Guide Popular Mechanics Discovery Entrepreneur Washington Times eWeek Hack-a-Day ThreatPost RT PC Mag Slashdot ComputerWorld Mother Jones
That’s a ridiculous amount of air time for a broken perl script.
Likewise, the skyjack videos start with the camera pointed at the author’s face and mostly are him being a talking head. Social entry feels like an understatement for attacker motivation here.
In any case within hours or release, he was forced to update the code when Afan Ottenheimer spotted bugs in the code and easily knocked skyjack out.
I tweeted about it December 4 of 2013 and while that led to a fix and initial credit, the author then removed credit to others and covered up that flaws were reported by defenders publishing the incredibly stupid class of bugs in skyjack:
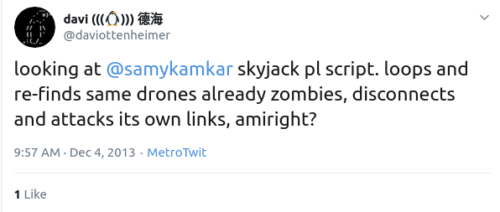
As I said before, attackers are riddled with vulnerabilities, are inexpensive to counter-attack, and penalties…well, they may be minimal if discovered but you can be sure attackers also don’t give anyone else the kind of credit they crave.
Update March 4th: A defense analysis article called Error 404 reminds us of a 2007 infiltration of computer systems to disguise kinetic measures.
A cyber attack was delivered into the Syrian IADS which presented a false live recognised air picture to Syrian air defenders which masked the radar tracks of the incoming Israeli jets.